In today’s fast-paced business landscape, effective communication and collaboration are essential for success. Traditional phone systems no longer suffice, especially as remote work and global teams...

deycom_1q68j0
How to protect your employees from Phishing Emails
Phishing is when cyber criminals try to trick an email recipient into thinking the email they have received is from someone else, and they will then try to get that user to reveal sensitive...
Backing Up Your Data – Best Practices
Backing Up Your Data – what are the best practices How to protect your valuable data Data loss can happen at any time. Someone might inadvertently delete some files on their computer, a hard disk...
RMM – Minimizing Downtime, Maximizing Profits
Deycom offers essential IT hardware, ensuring cost-effective solutions with tailored options. Consider factors like size, mobility, and specs, including processors, RAM, storage, and graphics cards. Prioritize desk comfort and ergonomics.
Thinking of Changing Broadband Provider – here are some things to consider
It makes sense to change broadband provider if you can get a faster internet connection, or you can get a better price from your new service provider. However, there are some technical...
Remote Managed Monitoring Updates
New Security Options available with Deycom Remote Managed Services Remote Managed Monitoring (RMM) is an incredibly powerful application with a range of security features designed to help protect...
Remote Managed Monitoring Updates
Choosing the right IT hardware is crucial for a robust infrastructure. At Deycom, we excel in IT solutions and managed provision, tailoring options to meet your specific needs. Whether it’s screen size, mobility, or technical specs like processor and RAM, we simplify the jargon. Desk comfort, or ergonomics, is vital for efficiency. Acquire your computer or laptop from us for optimal tools at competitive prices.
Changing Broadband Provider
Choose Deycom for tailored IT solutions and hardware. We simplify complex specs, ensuring your computer meets your unique needs without breaking the bank. From screen size to mobility, we’ve got you covered.
The Lenovo ThinkBook 15 G2 featuring Windows 11
If your are looking for a professional high-performing laptop that combines a 11th Gen Intel® Core™ processor with powerful graphics, the ThinkBook 15 G2 is the choice for you. This stylish, secure...
Lenovo ThinkBook 15 G2
The Lenovo ThinkBook 15 G2 featuring Windows 11 If your are looking for a professional high-performing laptop that combines a 11th Gen Intel® Core™ processor with powerful graphics, the ThinkBook 15...
Digital Transformation – Key points for driving digital transformation in your business
Digital Transformation - How to drive digital transformation in your business Digital transformation is on everyone’s lips now and can encompass so much, in essence, it is when you cleverly...
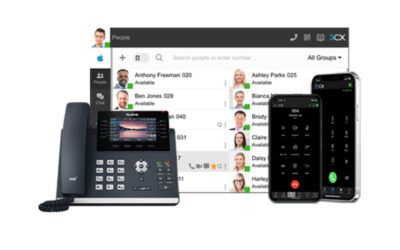
3CX VoIP Phone Technology
3CX, World leading VoIP technology Voice over IP phone systems are far from new, but the technology in this field means that the best VoIP systems on the market today are miles ahead of the more...
Choosing the right computer for the job
Choosing the right IT hardware is equally as important and ensuring you are operating a robust IT infrastructure.
For both, it is imperative to consider how you are going to use your IT and what daily functions you need to use it for.
At Deycom, we are not only experts in the field of IT solutions and managed IT provision, but we have the finger on the pulse of all thing’s hardware. Purchasing your computer online or via the high street is quick and easy, but are you getting the computer you really need?
One of the major benefits of acquiring your new computer or laptop from Deycom, or indeed any of your IT hardware, is that we can prescribe options that are en-pointe when it comes to meeting YOUR own personal needs. And despite popular opinion, when buying your hardware from an IT company like ours, it need not be more expensive that the alternatives. What it does guarantee is that you will have the right tool for the job.
Screen Size is very important based on how you like the visuals to be presented when at your desk, what tasks you are undertaking, whether you need more than one screen.
Space and Location. If you move between your office and alternative locations, what options are available in terms of docking stations for computers or plug and play scenarios if your business operates hot desks.
What is under the hood. Computers come with a log list of technical specifications that are ultimately related to how well the computer will function for you in terms of speed, memory, battery life for laptops and graphics. If you have every looked at a computer spec, you like so many other people probably wonder what it all means.
It essentially deciphers whether computer will deliver what you need – it is just a shame it is not available in plain English!
For example.
• Is the processor capable of working with your programmes and at the speed desired? The processer provides the instructions and processing power the computer needs to do its work. The more powerful and updated your processor, the faster your computer can complete its tasks. By getting a more powerful processor, you can help your computer think and work faster.
• How big is the RAM ( the short-term memory) and does it meet your needs?
• Do you need an internal hard drive or are you best suited to having an SSD
• What about the graphics card ?
Rather than regurgitate the technical specs, we are just giving you food for thought and an understanding as to why it pays to lean on someone ( us!) who can decipher the jargon for you.
Desk Comfort or ergonomics as the experts call it incorporates everything from how your eyeline meets your screen through to the streamlined design of wireless accessories such as your mouse or keyboard.
Having the right tools for the job is imperative no matter what you are doing and for that reason, having the right computer for you and your team is critical to the success and efficiency of your business.
To obtain information, options and a quote for your computer needs. Contact our team today
sales@deycom.ie
Zero Trust Network Access (ZTNA) the better alternative to VPN?
3D illustration of a blue network with icons and the text zero trust written on the front. Black background. Concept of secured network.
Blackpoint Cyber Security – Prevention over cure, unrivalled managed detection and response for your cloud-based data.
Blackpoint Cyber, Impenetrable Cyber Security For a Cloud Hosted World Prevention over cure, unrivalled managed detection and response for your cloud-based data. We are huge advocates for the...
Video Conferencing and Digital Whiteboards for a new way of working
Video conferencing and digital whiteboards for a new way of working In a recent Linkedin post, I shared an article that looks at the Zoom v Teams debate – it probably will become as marmite as macOS...
Migrating from on premise servers to cloud servers
Migrating from on premise servers to cloud servers, not the challenging task you might imagine. For as long as there has been cloud storage, we have been strong advocates for the benefits of cloud...
The Cost and Impact of Human Error and what to do about it?
Human Error and the simpler side of the spectrum None of us are perfect, and mistakes happen but when we review some of the most common IT issues we encounter, we are seeing a pattern. Simple errors...
The Ever Evolving Nature of Cyber Crime – Are you adopting best practices ?
Constantly evolving and ever prominent, the latest trends in cyber security and what that means for your business, especially with a notable increase in a flexible workforce.
In this article, we summarise the four most pertinent areas of cyber security and why you need to give each of them consideration in respect of your own business environment.
Office 365: A guide to the recent updates that were rolled out by Microsoft.
Office 365: A guide to the recent updates that were rolled out by Microsoft On April 26th, Microsoft rolled out an update for Office 365 / Microsoft 365 for Windows, and today we will share with you...
IT Solutions for your hybrid workforce
Post-remote work, companies embrace flexibility with hybrid models. We empower seamless transitions from office to remote work by extending robust IT infrastructure beyond physical boundaries. Our win/win solutions prioritize security, continuity, and a smooth experience for clients.
Employee cyber security awareness
Employee cyber security awareness Employee cyber security awareness In Deycom we see a lot of attempted Phishing attacks, where someone has tried to send a scam email to the employees within an...
Recycling your old computer hardware (and paper!)
Recycle your old IT equipment Remember to remove all data from old hard disk drives Overtime most organisation can build up quite a collection of older IT equipment including desktops, laptops, old...
What is Cyber Security
What is Cyber Security When you think about home security you can appreciate that you have multiple options to keep your house secure. You can have a simple lock on your front door, you can install...
Business Continuity and Disaster Recovery (BCDR)
Business Continuity and Disaster Recovery (BCDR) What is BCDR and why is it important? The majority of organisation's know they should be backing up their critical data. What is sometimes forgotten...
RMM Software, What is it and why you need it?
RMM Software - What is it and why you need it? Prevention is better than the crash! It is nearly impossible in this day and age to work without technology. Individuals expect an instant response to...
Microsoft patch update and printing issues
Microsoft patch update and printing issues Microsoft Windows 10 is a very robust operating system and it rarely has any issues, especially the famous Blue Screen of death. It is considered best...
Ransomware, the one IT issue you cannot ignore
We take IT security very seriously in Deycom and our number one concern is stopping Ransomware attacks. Thankfully, a lot of the security measures that most businesses have in place such as...
Targeted Ransomware Attacks on the Increase
Targeted Ransomware Attacks on the Increase In today’s computer-driven business environment, Ransomware remains the single greatest threat facing any business that relies on its IT infrastructure....
3CX in the Cloud
3CX in the Cloud - Take back control of your Phone System. 3CX is an open-platform, software VoIP phone system that works with popular IP Phones and SIP trunks. Offering a complete Unified...
Backing Up Your Data – what are the best practices
Backing Up Your Data – what are the best practices How to protect your valuable data Data loss can happen at any time. Someone might inadvertently delete some files on their computer, a hard disk...
ESET DESlock Encryption
Don't Risk Data Breaches DESlock Encryption by ESET : Your best choice Data security has always been important and with the new GDPR regulations coming into force in May 2018 it is more essential...
Lenovo V330 Notebook
Lenovo V330 laptop Thin and stylish with a 180-degree hinge With the Lenovo V330 laptop, you can stay value-focused without sacrificing performance and reliability. It features a simplified...
SSL Certificates
What is an SSL Certificate? And if you own a website why you should care? Have you ever noticed in the address bar of your browser that some websites start with the letters HTTPS:// and they have a...
GDPR Event
Getting Ready for GDPR Deycom Computer Services was delighted to host a successful GDPR Event on the 29th of March aimed at helping organisations prepare for the new data protection regulations that...